Security of any type of cryptocurrency exchange platforms remains always of paramount importance. Nonetheless, there have been numerous instances of crypto exchange hacks in which users lost their cryptocurrencies of worth over a billion dollars. Not only these exchanges store cryptocurrencies, but they also use personally identifiable information (PII) of users without their consent. In addition, any malicious activity or hacking also exposes sensitive information like personal addresses and other identification details to vulnerabilities. Altogether, it hinders the widespread adoption of crypto exchange software solutions. It leads to consequences like manipulation of data, privacy infringement, unguarded crypto storage, and so on.
To address and overcome these security challenges, crypto exchange development company must ensure that they implement commercial-grade security implementations. The developers should follow the agile development method to ensure the security of the platform, currency, and user privacy.
DoS (Denial of Service) attacks are one of the most sweeping challenges that crypto exchanges experience. DDoS protection and X-frame-Options are some of the basics security practices that protect against DoS attacks. According to research, approximately 80% of crypto exchange and trading platform use DDoS protection and more than 65% of exchanges guard themselves with X-Frame-Options. Other security measurements crypto exchange investors must consider are Strict Transport Security, X Content-type, and X XSS protection.
Protective security measurements to implement to make a Cryptocurrency exchange safe and secure
DDoS Prevention

Distributed Denial of Service disrupts the network connectivity of a system and results in the denial of service for users.
- Overloads the system with distorted requests produced using SSDP and NTP amplification
- Attacks and disrupts the application layer
- Damages the connection table that validate the connections of the network
A DDoS attack often combines these three methods to bring the crypto exchange platform to a standstill and disrupt the entire system.
Taking preliminary caution like defining the traffic pattern can enable strong security around the platform and prevent DDoS attacks. Filtering the traffic route can enable the detection of abnormal traffic produced by malicious bots. Filtering uses techniques like deep packet inspection, IP reputation lists, and connection tracking. Scrubbing is an efficient filtering method.
Techniques like rate limiting, port blocking, regular expression filters prove to be quite effective in preventing SSDP and NTP amplification attacks. Faulty traffic sources are prevented by eliminating the UDP fragmented packets from the sources. Any change in the flow of normal traffic can be tracked with traffic signature filters. Eventually, some parts of the exchange platform must be removed or blocked, including DNS’s TCP and UDP port 53. These are some of the common targets for hackers.
X-Frame-Options

Clickjacking is another common security challenge that inhibits the user interface of the exchange platforms. Clickjacking is a practice that hackers use to mask the interface of the exchange with layers of clickable buttons that are not actually visible. When users click on these buttons, it redirects to other fake websites where they mistakenly expose their private keys. In a nutshell, users think that they are typing on the original page of the exchange. In reality, they type their private key details on the hacker-controlled user interface.
X-Frame-Options display specific pages by controlling the browser. It produces a
response header, an element of the HTTP response of a webpage with particular tags
like
<Header set X-Frame-Options "deny">and <Header set X-Frame-Options
"allow-from https://example.com/">.
X-Frame-Options prevent any misleading domain to show in the frame and enable only defined pages to be displayed on the website of the exchange.
Strict Transport Security
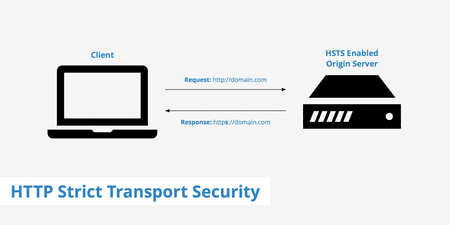
Implementing Strict Transport Security Header enables the exchange platform to push the browser to load the website only with HTTPS. It diminishes the risk of any man-in-the-middle attacks using redirection of requests to the original crypto exchange platform.
Cryptocurrency Exchange Security Assets
- Two-Factor Authentication (2FA): Adds an extra layer of security the safety of online accounts
- Ledger Encryption: Uses strong cryptography practices to ensure secure financial transactions, controlled creation of extra units, and accurate validation of assets transfer
- Anti-Phishing system: Recognizes phishing content within websites, email, or other forms. Protects exchanges from phishing attacks that try to access data
- Multi-sig Vaults: Enable self-sovereignty that provide users with secure and controlled access and use of their private keys and digital assets
- Cold Wallets: Provide secure storage of users private and public keys. Protects the wallet assets from unauthorized access and cyber hacks
- Log Tracking Tools: Enable enhanced log management, monitoring, and analytics. Address security-related concerns by identifying the primary reason for the functionality error of the application, within a single query
Improve Security of Your Crypto Exchange with Oodles
Oodles is a leading crypto exchange software development company in India that also excels in crypto exchange software development. At Oodles, we ensure optimal security of the exchange platform by implementing the right security practices, including the ones mentioned in the article. Our crypto exchange development services, including the white label solutions with ready-to-use modules, provide overall protection and security of crypto assets and user information. Crypto exchanges developed at Oodles enable investors to build strong market reach and credibility for global adoption of the business.





